
Phishing Emails: Everything You Need To Know To Protect Your Business
Email phishing is one of the most common cyber threats, and yet many businesses still fall for even the most basic phishing techniques.
In this article, we are going to answer the question: how do you protect yourself from phishing? Protection from email phishing is a combination of knowing what the common phishing techniques are and implementing defense strategies that would save your inbox (and network) from harmful attacks.
What Is A Phishing Email?
A phishing email is a type of cybersecurity attack used to steal data or gain access to an organization’s network. Phishing emails are usually targeted to lower-level employees to acquire login credentials, company data, and other sensitive information. Hackers can obtain gateway information that will help them penetrate an institution’s defenses.
Phishing emails can also be used to infect endpoint devices with malicious code. Links in these emails can lead to malicious websites that will install malware into the system, which hackers can utilize to initiate attacks.
Email Phishing In Numbers
- Email phishing is the leading cause of data breaches. Almost one-third of data breaches stem from a phishing attempt.
- One of the most common phishing emails involves Dropbox. These emails typically have a 13.6% click-rate
- Even Microsoft Office files aren’t safe. 48% of harmful email attachments come as Office files.
- 66% of malware is installed by clicking a link in a malicious email or opening an email attachment.
Email Phishing: Who Is At Risk
- Low-level employees: Clerks, secretaries, customer representatives, and similar members of your organization are common targets of email phishing because hackers assume they don’t know any better. These employees usually have access to customer data, passwords, and other sensitive information.
By taking advantage of these employees’ ignorance or laziness, attackers can get the information they need to launch more complex attacks. All it takes is for one unsuspecting employee to click a link, and this malware can take hold of your business’ entire network.
- Small business owners: Too many small business owners make the mistake of thinking that their business is too small to be on anyone’s radar. This is especially true for businesses with less than five people or solo entrepreneurs who are eager to open fake customer inquiries, job applications, and other interactions through email.
How Do You Know An Email Is Fake?
To the uninitiated, phishing emails look completely legitimate and valid, which is exactly why it’s so easy to fall for them. Back when phishing attempts were a little less sophisticated, common tells include:
- Grammatical errors or inconsistent grammar
- Misspelled words
- Incorrect punctuation
- Improper formatting (double spaces, weird indentation)
- Complicated URLs
- No branding or signature
- Unknowing sender address and website
Nowadays, a phishing email can look completely legitimate, complete with branding (logo) and even a seemingly valid email address.
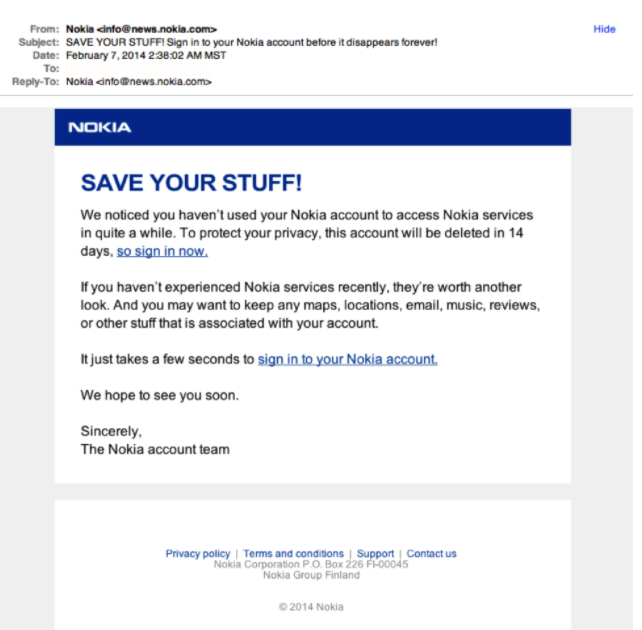
The good news is that there will always be small details that reveal whether or not the email is malicious. One way to do it is to look for inconsistencies in the messaging. For instance, a company like Nokia wouldn’t be so informal with its customers.
The line “And you may want to keep any maps, locations, email, music, reviews, or other stuff that is associated with your account” is a clear indication that email was sent by a non-affiliated third party group.
Next, take a look at the sender’s address. Even if the sender mentions the brand, keep in mind that companies (even the small ones) use their own domain. Legitimate emails will come directly from marketing@nokia.com or sales@nokia.com, not info@news.nokia.com. Extended domains such as signin.portal.facebook.com or infouniversityportal.com are designed to trick users into thinking these are legitimate domains. When you see convoluted email addresses, try to verify with the supposed sender (if the email is posing as a familiar contact) or consult your IT department.
Finally, the signature reads “The Nokia account team”. Emails concerning customers are sent by customer representatives, who are obligated to sign with their names and their position so they can be properly identified. This may be a small detail but the inconsistency in the lower case ‘a’ and ‘t’ are telling that this was not sent by an official member of the Nokia company.
Those are just some ways of telling if the email you received is a phishing email. Ultimately, you need to pay attention to all the details in the email to determine if it’s malicious. Here are some things you can take a look at:
- Domain (sender@website.com)
- Sender name
- Inconsistencies in style, body, messaging, formatting
- Unknown characters (the greek letter α in place of a to fake domains)
- Links and attachments
What Are The Common Forms Of Phishing?
If you thought phishing emails were a big company problem, think again. Small to medium businesses are among the main targets of fake and spam emails precisely because hackers know these businesses don’t have the security in place to protect their systems from an attack.
Regardless of how big your organization is, the phishing techniques are generally the same. The first step to preventing hackers from accessing your system is understanding common phishing techniques:
Posing As An Angry Customer
A strong sense of urgency can mobilize employees to act rashly. A hacker posing as an angry customer works well in most cases since customer reps may feel the pressure to respond to the inquiry without validating the request.
Common tactics include attaching malicious attachments and links masquerading as important documentation, which can include bank statements, receipts, and even authorization letters allegedly authorized by company executives.
Installing an anti-malware system that will scan all documents and links is imperative in keeping your inbox safe. Before clicking links, make sure to hover without clicking, which will display the real link address on the bottom left corner of your screen.
Angry “customers” may also request password changes and documentation, applying pressure to employees to expedite the process. One of the best ways to verify this kind of request is to put a multifactor authentication in place. Ask customers to verify their identity with government IDs, transaction history, and password to verify that you are working with customers only.
Email From An Executive
Phishing emails don’t always come from the outside. It’s easier to fall prey to these hacking schemes if you think your boss is asking you to carry out a task. As with the customer scenario, the same psychological trick works here: because the email is coming from an executive, employees rarely want to verify to avoid seeming redundant or unreliable.
Executive requests often come in the form of money transfers or sharing of login credential details. Before executing these commands, ensure that the email domain is a valid one. To be safe, it’s always good practice to verify with your boss on-call or in-person before processing huge amounts of money or handing over other sensitive information.
Vendor Or Partner Email
Emails from other service or product vendors and partners may be subject to even less scrutiny, especially if your business has a longstanding relationship with them. However, it’s exactly this trust that hackers use as leverage in order to penetrate your business’ defense network.
Big companies like Apple and Amazon have been used as bait to hook in unsuspecting employees. Hackers typically use scare tactics like account deletion or raising an alarm over account security in order to get an employee to click through a link or download an attachment.
When dealing with partners or vendors, use secure platforms for money transfer and documentation. Whenever major problems arise involving payment or logging in, call the vendor representative to verify the request using phone numbers and emails on the official website (not what is suggested in the email), or forward the email to a manager or supervisor for verification.
Zombie Emails
Zombie phishing is a new type of tactic where hackers use compromised email addresses to reconnect with old contacts. Because the sender is familiar, victims instantly trust these email addresses and whatever content that comes with it.
Before responding to old contacts, pay attention to the consistency of their message. Look through old email threads to verify whether the email is a phishing hack or a legitimate email. Be especially vigilant of email contacts that have been inactive for more than three years. Phishers will usually send a new email using an old thread in order to reinforce the idea of security. As always, practicing multifactor authentication will help you verify the identity of the person you are supposedly in correspondence with.
What To Do When You Get A Phishing Email
Phishing emails can’t harm your computer by being simply in your inbox. Some form of interaction — whether it’s clicking the link, clicking the button, or downloading the attachment — is necessary to initiate the malicious attack.
When you receive an email that you suspect is some form of phishing, the best thing to do is to get in touch with your IT department. They can help distinguish whether the email is fraudulent or not.
As a business owner, implementing cybersecurity measures such as anti-virus and anti-malware installation on all endpoint devices are non-negotiable when it comes to protecting your data.
Just as important, however, is regular employee training. At Abacus, we conduct phishing training to give employees on all levels insight on what a phishing attempt looks like. With regular testing, we can instill vigilance on employees and train them to be more watchful when dealing with emails and other forms of electronic correspondence.
What Is The Best Defense Against Phishing?
A robust cybersecurity network can protect your inbox, but the best defense practices are still dependent on employee behavior.
There’s only so much software can do to safeguard your computer from these harmful attacks. At the end of the day, the best defense against phishing is not falling for them in the first place.
Verify With The Sender
For unusual or unprecedented requests, verifying with the sender is always the best way to go. Contact them through a verified channel (phone, social media) to see whether the email is real or not.
Hover Over The Link
Links are always not what they appear. In order to shorten complicated URLs, hackers can use services like Bitly to generate anonymous short links, which won’t reveal much about the link’s location.
Always hover over the link to ensure that the link address is the same as what has been pasted. Here’s an example:
A link may appear familiar and significant like www.facebook.com only to link to a malicious third-party site. If you hover over our example link, you’ll see that the real domain is facebook.notreal.com. Pasting links for “transparency” purposes and hiding the real address is a common tactic to get users to click malicious links.
Don’t Open Any Files
Don’t open files from untrusted senders. Run emails through an anti-virus program so they can scan the attachments before they are downloaded. For safety purposes, it’s better to ask unknown contacts to attach their photos and similar documents as in-line instead of an attachment.
Don’t Trust SSL Certificates
Not all phishing websites look gaudy and terrible. Nowadays, phishing websites look exactly like the website they’re copying. To verify the site, most users look at the SSL certificate or the little padlock next to the domain, which supposedly assures that the website is legitimate.
In reality, the SSL certificate doesn’t guarantee that a website is not a phishing site. SSL certificates are relatively easy to obtain. Anyone who wants to build a website only has to pay for it as an add-on. So the next time you’re redirected to a suspicious website, check out the little details on the site (without clicking anything) to verify whether it’s real or not.
Email Security In A Nutshell
At the end of the day, email security starts with knowing the best practices for dealing with electronic correspondence. Diligent employee training and a reliable anti-malware system are what you need to protect your business from malware attacks. Having a disaster recovery plan will allow you to revert to previous versions of your system, should a malware attack prove successful.