Remote Access Scams: Everything You Need to Know to Avoid Falling for One
Remote access technology is essential in maximizing the efficiency of IT departments. It allows the team to provide support to businesses even in significant physical distances. But as easy as it is for tech support to be delivered, this technology is also a niche for remote access scams.
But what are remote access scams? With remote access scams, hackers contact the victims and obtain access to their computers by disguising as tech support providers. Once they enter the network, they can start stealing money and other useful data that can be used or sold.
Organizations and individuals can protect themselves against hacking by looking out for suspicious calls and messages, restricting network access, regularly updating the system, and installing protection against malware.
What is Remote Access Hacking?
Remote access hacking happens when scammers and hackers break into vulnerable servers, devices, and networks. By gaining access to the networks or devices, they can start stealing information like bank accounts, confidential company information, and even personal data. While this kind of hacking is fairly common, there are still people who fall victim to remote access hacking schemes.
What Can Remote Access Hackers Do to Your Computer?
Hackers essentially have full control of your computer after they enable remote access on your device. Remote hackers can install software that blocks your screen, shares your desktop, or registers your passwords through keyloggers.
Aside from utilizing the information for their own benefit, they can also use the access as leverage to ask for a reward payment, more commonly known as “ransomware.” On top of holding crucial data ransom, hackers getting into work devices typically sell their assets and information on the dark web.
Common Types of Remote Access Hacking
To protect yourself against these scams and attacks, it’s important to be familiar with how remote access hacks work and what the scheme typically looks like. Here are three examples:
Remote Desktop Protocol (RDP)
Remote Desktop Protocol (RDP) is commonly used by organizations to allow remote work. But when one endpoint device is not secure, the whole IT system becomes vulnerable to cyberattacks. Hackers utilize online scanning tools to search for these vulnerabilities in the RDP endpoints.
The biggest problem with using RDP for remote work is that it cannot differentiate between bad and good actors once they enter the network. This makes it easier for hackers to collect company information without being detected.
Remote Access Trojans (RATs)
Aside from gaining access through stolen credentials, hackers may also use different malware types such as the Remote Access Trojans (RATs). This method involves phishing campaigns where hackers will send files or links to the client. Once the malware has been installed on the victim’s device, it gives the hackers back-door access to the private network.
In a remote work environment, victims might think RAT is just another program required for a work from home setup, avoiding detection from the employee or even administrators.
Automated Malicious Bots
More and more organizations are starting to use artificial intelligence and automated bots for different purposes. While they are certainly helpful for the company, hackers can also use malicious bots for ill intentions.
Compromised bots can scan the website, apps, and APIs for weak security spots they can utilize for entry.
How People Fall For Remote Access Hacking
Hackers employ different tactics to trick their victims. Spotting these tell-tale techniques as early as possible can keep you from falling for one:
Phone Calls
Remote access scammers usually disguise themselves as computer technicians from well-known companies like Microsoft, Telstra, and NBN. They will tell victims that there is a problem with their computer; it might be a connection issue or malware infection. They might also talk in technical language to intimidate the victim into following the instructions.
They will pretend to run a diagnostic test and ask for remote access to the computer. Once they obtain the needed details, they will charge the victims for fixing a problem that doesn’t exist.
To become more familiar with how a phone call with a tech support scammer sounds, here is an excerpt from the Federal Trade Commission. The scammer claims that the computer is infected even though the warning message appears on most computers.
Pop-up Warnings
Scammers also lure victims in and make them call first by using false pop-up windows. These pop-up messages often look like error messages with logos from trusted websites or companies. It will warn victims about a security issue on the computer with a phone number where they could get help.
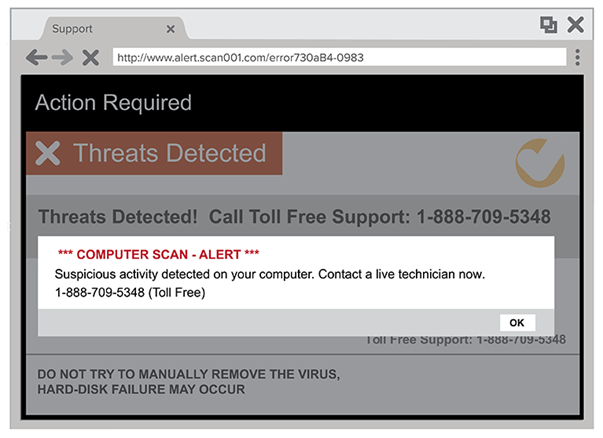
Here’s also a more detailed example from a Youtube video uploaded by Jim Browning. In this video, he calls a number from a company called TechKnacks IT Solutions LLC who claims to fix computer problems. The scammers used a remote access software that can freeze the screen and take over the victim’s controls over their computer. They also tried to make the victim pay $200 for fixing a problem that doesn’t exist.
Online Ads and Listings
Some scammers also try to get their sites to show up in the search results when people look for tech support. They can also run their ads online, hoping that victims will call them for help. If you need tech support, it’s better to get them from a trusted company that you know.
Signs That Your Computer Is Infected
Most of the time, victims don’t realize the scam as it is happening. To see if your network or device has been hacked, here are a few signs to watch out for:
- Computer functions start moving on their own; your cursor starts moving without your control and applications might be downloaded without your consent
- People receive strange messages from friends and colleagues
- Some of your files have been encrypted
- Odd redirections to ads and dodgy sites pop up once the browser is opened
How to Prevent Remote Access Hacking
Remote access hacking can bring severe damages to the victims. To prevent these kinds of hacking from happening, creating a multi-layered security approach is necessary. Here are some methods that organizations and individuals can employ to prevent hackers from gaining access to their devices:
Looking Out for Suspicious Calls and Messages
If someone calls about a tech issue and asks for remote access, hang up immediately. Always remember that companies do not ask for credit card details over the phone to charge victims for fixing computer problems.
Some pop-up windows created by scammers also look realistic but keep in mind that a legitimate malware notice wouldn’t include a number to call. Aside from personal information and bank account details, hackers may also attempt to ask for remote access to the computer.
Restricting Access
There are many ways to restrict access – changing the default setting, preventing guest accounts from entering, and using two-factor authentication.
By changing the default username, hackers will have a hard time trying to guess the username and password for the network. Using a combination of characters, symbols, and numbers can help limit access and minimize the risk of network hacking.
Guest accounts can allow anonymous users to access the device and network. Disabling these accounts can protect the company against unauthorized users who can launch remote access attacks. With guest accounts, it’s easier for bad actors to install the malware in the device or the network.
Two-factor authentication is a verification process that effectively secures remote access networks. To access the device or network, users need to input their username and password, as well as a random security code that will be sent to the email associated with the account.
Updating the System
Frequently updating the system can also prevent unwanted access through vulnerable backdoors. Aside from patching up the vulnerabilities from the previous version, system updates also provide the latest features and functionality of some apps for added protection.
When upgrading the system, make sure that all needed data is still secure and the necessary software for company operations is still compatible.
Installing Protection Against Malware
Downloading good anti-virus software can also help the early detection of malware. Make sure that all anti-malware programs are updated according to the system and that they regularly scan the device and network. Early detection of malware can prevent a couple of remote access attacks from happening.
Before settling for antivirus software, consider the following:
- Price
- Download Protection
- Virus and Malware Scans
- Speed
- Compatibility
- Privacy Policy
Implementing Vulnerability Scanning
Vulnerability scans test the networks and system to find weaknesses. A complete scan will produce a detailed report about the specific weaknesses found in the systems and networks. Using these reports, IT experts can fix the vulnerabilities as soon as it is detected.
Protect Your Data Privacy with Abacus
Here at Abacus, we ensure that our clients are well-protected against malware and other tech issues that can potentially damage their organization. Our wide range of services can offer comprehensive protection and support for your remote access needs.
To avoid getting scammed by remote access hackers, contact a trusted provider like Abacus for all your IT solution needs. Learn more about us and how we can protect your data by visiting our website.