
What To Do After Opening Phishing Email
If you think phishing emails aren’t as damaging as they sound, think again. 90% of data breaches come from clicking a phishing link, with damages varying from theft of personal information, breach in network security, to data loss.
With phishing scams becoming more sophisticated, it’s proving more and more challenging to distinguish between a phishing email and a real one. If you ever fall prey to one of these scams and end up clicking a phishing link, how do you reverse the damage, if at all possible?
In this article, we discuss the steps you should take after falling for a phishing email. These precautionary steps aren’t meant to undo the damage, but limit its impact on your business network. While nothing beats getting your endpoint device getting looked at by a professional, these immediate actions may help save crucial personal information and business data from being corrupted forever.
Signs You Fell For A Phishing Tactic
The danger of modern day phishing attempts lie in the fact that they don’t appear like scam emails anymore. Nowadays, hackers can compose convincing phishing emails and phishing sites that are designed to make you click without a second thought.
What’s even more alarming is that attackers may have already succeeded in installing spyware and malware, executing malicious code, or stealing your credentials without your knowledge.
Some installations are outright which can occur right after you download infected attachments (.zip files, Microsoft Office files, PDFs), while others might run quietly in the background.
Even ransomware attacks, which is a rising cybersecurity threat involving the use of encryption tools to lock the user away from the computer as well as all of its data, aren’t always obvious. There are reports of “delayed” ransoms wherein the user restarted the system a number of times before the encryption process began.
So watching out for specific signs isn’t entirely useful because today’s cybercrime landscape has made it difficult to predict how phishing attacks operate, precisely because attackers have developed more sophisticated and subtle ways to hijack your computer network.
Not to mention that noticeable changes in your computer network might mean that it’s already too late.
Taking Action Before It’s Too Late: Is It Really A Scam Email?
The best way to determine whether you’ve fallen for a phishing email is not to wait for the signs but to verify if the email, link, or message was genuine in the first place. If the email, text message, link, or website isn’t from the verified source, you can safely assume that you have just fallen for a phishing attack.
Here are some things to watch out for:
- Familiar Email Address: An email from an old colleague, a former employee, a product or service vendor, or even the company’s CEO means the email is 100% safe, right? Not really. Hackers could easily take advantage of compromised emails and use their address book to send out a phishing link. Instead of taking the “sent from” section at face value, verify the sender by checking out the real email behind the name or asking the sender to make sure the email or text really came from them.
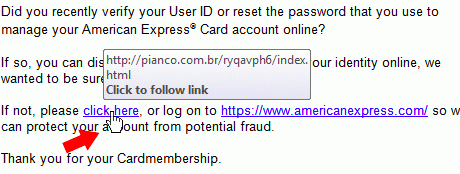
- Links and Buttons: Phishing links can be disguised behind buttons or seemingly harmless links. Before clicking anything, hover on the button or the link to reveal the real link destination and make sure it is a secure address.
Keep in mind that link phishing involves the use of copycat addresses (facebook.signups.com for Facebook as a dupe log in page, or using .org and .net instead of the .com equivalent) so read through links multiple times before clicking.
- Flag Suspicious Behavior: Co-workers sending funny video links through email, CEOs requesting their own login credentials, or reminders on unpaid invoices are just three of the most common phishing techniques.
Don’t just think about the content of the message; think back to its intent and whether it makes sense for the sender to make this request. If invoices are paid through a secure portal, why would vendors or customers request one through email?
What To Do After
Let’s say that the email was indeed fake – does it mean it’s over? The most effective course of action is to notify your IT department immediately to ensure that all malware is effectively removed from your device.
On the other hand, there are some steps you could take to limit the spread of the malware and contain the damage however you can. Here’s how:
- Disconnect From The Network
Think of computer malware like any other human virus; those in close proximity with you will get infected. You can reduce the infection rate by cutting off all contact. In this case, you can limit the effects of the malware to your computer network by disconnecting your computer or phone from the internet connection.
This achieves two things: first, disconnecting from the internet cuts off your endpoint device’s response with the hacker. With no signals coming in or out, they are unable to execute the commands and launch more sophisticated attacks while your device is offline.
Second, it prevents the malware from creeping into your computer network and infecting all other devices that are connected to that same network. Even if other endpoint devices have their own security measures in place, one infected device could easily bring down the entire network as attackers can exploit weak links in the system.
Not to mention that more sophisticated malware can bypass firewalls, antivirus systems, and other cybersecurity measures in place and infect other endpoint devices on your system. If you’re connected through ethernet ports, simply unplug the device to keep it offline.
- Secure Your Log-In Credentials
This is especially important if you typed out your login credentials on a phishing site or filled out some kind of form. Whether it’s a personal or company-related log in detail, secure all these by changing the username and password combinations to all your accounts immediately. This includes your personal account relating to your finances, social media, and email, among others.
If you shared financial information, call your bank immediately to prevent any withdrawals and purchases. Instruct credit card providers to freeze your account until the threat has been neutralized.
For company-specific credentials, notify relevant personnel that a certain login credential has been compromised so they can take the necessary steps to secure that account and keep important data under lock and key.
Exposed company login details are especially dangerous because attackers may use this as a gateway into the system. They can perform lateral attacks and gain more permission until they reach an admin account, allowing them to access for information and even disable security settings once the infiltration is complete.
- Run An Antivirus Scan
The point of running an antivirus scan is to track down and erase malicious files on your computer. However, doing so won’t guarantee that your device is completely risk-free. This is especially true if your computer’s first line of defense is the traditional antivirus, which have since been proven obsolete when pitted against modern-day cybersecurity issues like zero day vulnerabilities and current versions of ransomware.
To get the best level of protection, you need a next-generation antivirus (NGAV). This software is designed to hunt down all suspicious activity, regardless of the file type. NGAVs have additional functionality, most notably disrupting kill chain attacks, that prove useful in the face of phishing emails – a proactive malware-fighting feature that isn’t present in traditional antivirus.
- Backup Files Offline
The best way to keep your files protected is by storing a second copy of it offline, preferably on a thumb drive or a separate endpoint device that has no or limited internet connectivity. Ideally you already have a backup copy of all your files (or even your entire OS including apps and settings) prior to clicking the phishing email.
For hassle-free data protection, consider using cloud-based backups. This type of service performs regular backups with little to no intervention. It’s a great hands-off approach
- Forward The Email To Your IT Department
After taking these precautionary measures, forward the entire email (headers and footers) included to your IT department. They could use the information available to flag IP addresses and other pings associated with the phishing attempt. This will also help them develop courses and other guidelines on how to avoid falling for email phishing attempts in the first place.
I Don’t Have An IT Team – Now What?
Falling for a scam link is just one of the many looming threats to your business’ security. Having a dedicated team to reinforce your IT infrastructure doesn’t mean you have to have one in-house. For hyper-focused businesses that need smart protection, consider getting outsourced IT for all your cybersecurity needs.
Book a free consultation with Abacus today, and eradicate the weaknesses and vulnerabilities in your business computer network.