Categories
Account Takeover: Are You Opening the Door for Cyber Threat Actors?
Cyber criminals are constantly working to find ways to steal your personal information. When you’re not careful, you can find…
Can Ransomeware Infect Salesforce?
Salesforce is a great platform that provides efficient cloud-based services for many organizations and businesses. If you use Salesforce, it’s…
How are IP Reputation and Threat Intelligence Data Connected?
There’s a common misconception that IP reputation and threat intelligence data are unrelated, but they are actually connected in terms…
IP Geolocation As A Tool Against Cyberattacks
As the world advances in technology, people and organizations enjoy the fruits of being connected online. However, threats also exist…
Who Needs Cyber Insurance for 2022?
As the world continues to enter a new chapter in its storied technological history, the threats that come with the…
Rising Forensic IT Costs and How Cyber Insurance Helps Companies Save in the Long-Term
Data security is undoubtedly the biggest challenge for companies in contemporary times. A cyberattack not only compromises the data security…
Cyber Insurance Policies: Getting Started, Coverage Types, and Requirements
Cyber insurance policies are the need of the hour when most companies are transitioning into data companies. Nearly every company…
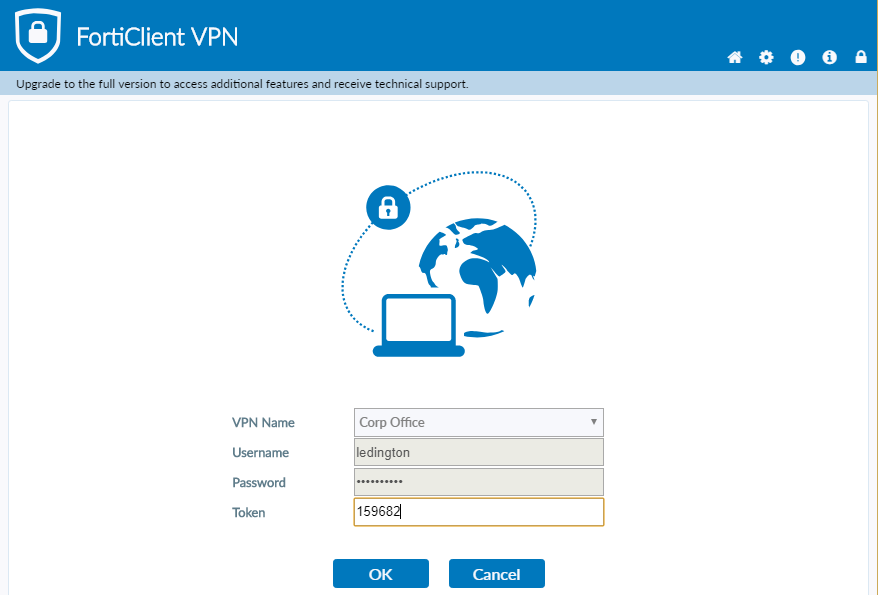
How To Access Corporate VPN Using Forticlient and Microsoft Desktop
Corporate VPN solutions have rapidly become essential for businesses that want to keep their data secure while still allowing their…
What Happens When You Don’t Patch Security Updates?
When you’re working on a project and a window pops up asking to install the latest update, you might be…
Should Your SMB Install a UTM Firewall?
More and more small and medium-sized businesses are utilizing network-connected devices for their operations, but this also means there’s an…