Resources
Why Disaster Recovery Plans Fail More Often Than Not?
Disaster recovery plans are developed with the intention to serve as a protective measure to keep invaluable data safe when…
Best Disaster Recovery Solutions to Preserve Company Data
Disaster recovery solutions are a crucial part of managing data and IT services in an organization. They help recover data…
How to Test a Disaster Recovery Plan
Testing a disaster recovery plan (DRP) is a crucial step to recover data and restore operations. Disaster recovery plans that…
The Best Backup and Disaster Recovery Software in the Market
Every business needs to think about disaster recovery because it ensures that your company returns to normal operations and isn’t…
The 5 Best Productivity Tools That Come Free With Your Microsoft 365 Subscriptions
Microsoft 365 represents some of the best innovations in cloud-based tools, especially for companies that want to maximize their productivity….
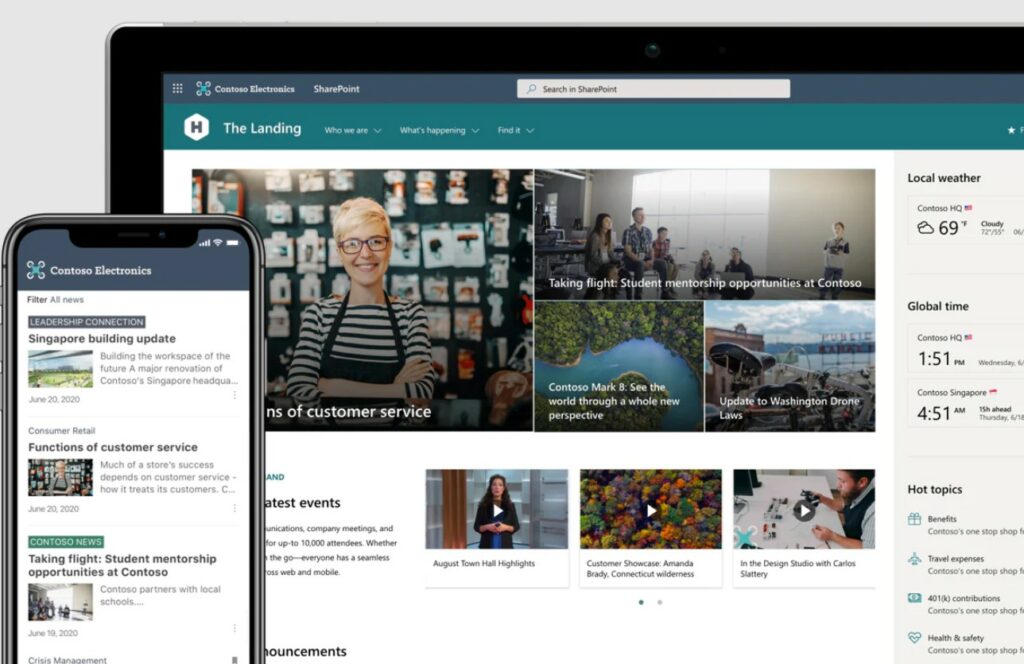
How To Streamline Information and Resources With Microsoft Sharepoint Online
Sharing information and resources is crucial to helping a company run smoothly. Fortunately, any company today has access to a…
Is Microsoft Teams Better Than Zoom?
Video conferencing and team collaboration tools have seen a rapid rise in use in the past two years, as more…
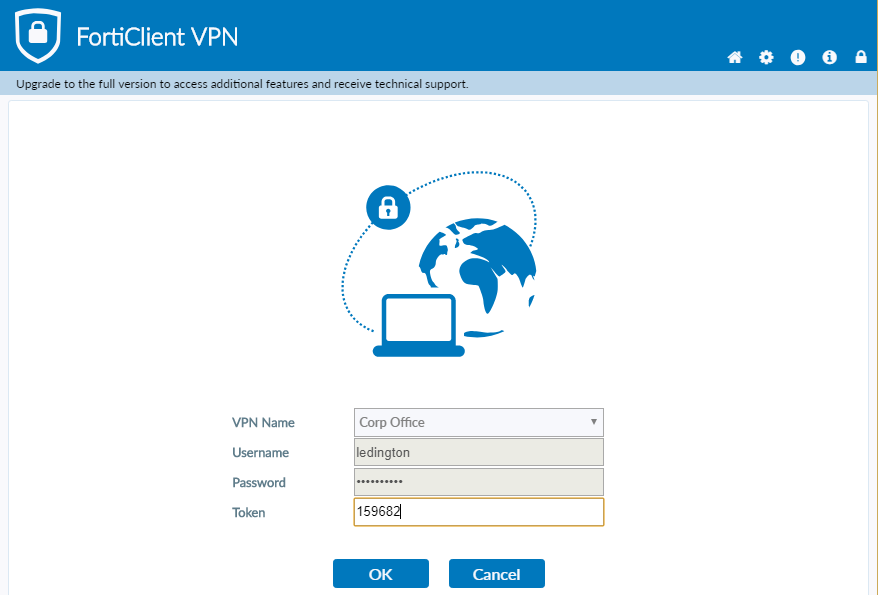
How To Access Corporate VPN Using Forticlient and Microsoft Desktop
Corporate VPN solutions have rapidly become essential for businesses that want to keep their data secure while still allowing their…
Abacus Services: Supercharge Your Projects With An IT Steering Committee
Navigating through the changing world of IT can be extremely confusing, but having an effective IT management team to help…